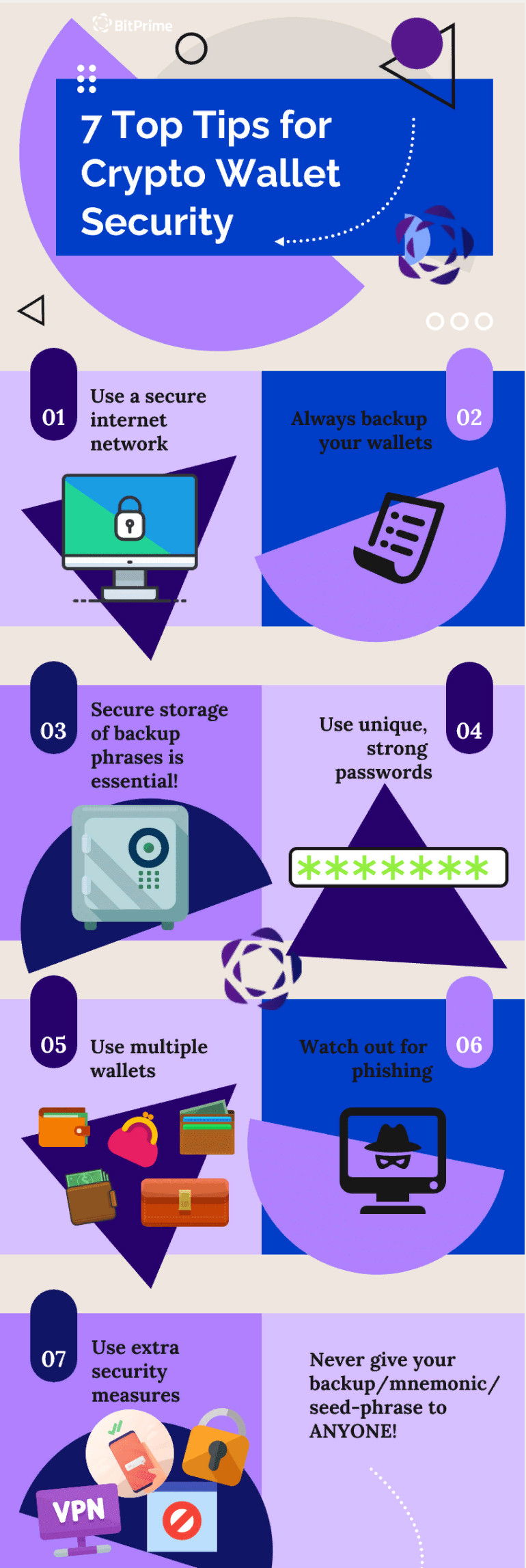
Top 7 Wallet Security Tips to Keep Your Bitcoin & Cryptocurrency Safe

Crypto wallet scams and hacks are on the rise. Here are some of the smartest ways to secure your crypto wallet from attacks by bad actors.
Every year, the hackers and scam artists who prey on the crypto community add new tricks to their arsenal of techniques. With 2022 having been one of crypto’s most exciting yet, loads of new users are now piling into the space, drawing the attention of malicious actors and software that cash in on their mistakes.
Let’s take a look at how criminals are trying to move in on your crypto and how best to stop them, including by keeping digital assets in cold storage – the only truly secure method.
We know there’s a good chance you might be using popular hot wallets such as MetaMask and TrustWallet, which have recently been targeted by a devastating new type of malware. Their direct connection to the Internet makes them especially vulnerable to attacks, as a quick search on Reddit boards littered with sad crypto stories will show. No software-based crypto wallet is safe, especially if you interact with DeFi and NFT protocols that require you to sign authorization approval and more.
Therefore, here are seven useful habits to use across the board for most crypto wallets, both hot and cold.
Oh, and If you don’t own a CoolWallet yet, please proceed directly to Tip 7!
FRAUD WITH BITCOINS AND CRYPTO: METHODS OF PREVENTIVE PROTECTION OF CRYPTO ASSETS
Tip 1: Create heavy-duty passwords
This should go without saying, but it’s essential to have an extremely strong password that is as close to random as possible. And you should never use the same one twice.
These days, if you’re unlucky, hackers making a brute force attack could use a password list stolen during a data breach to make educated guesses at your account credentials. Therefore, you don’t want to choose any words that aren’t totally random and disconnected from your life.
It’s also best to avoid password managers for your most important data, especially cloud or browser versions, as some have been breached in the past.
Tip 2: Avoid phishing attacks
Although it’s one of the older digital crimes out there, phishing is more relevant than ever in the age of cryptocurrency. The term refers to scam emails that, if opened, let loose malware giving the sender access to the receiver’s device. It’s important to regard any unidentifiable email – and especially attachments – with extreme suspicion and as a possible phishing scam.
Such messages may be disguised to look like they came from a particular company, but there will be differences. For instance, a big corporation will send emails from its exact domain name. And they will almost certainly never contact you by email to verify personal information. This extends to companies in the crypto space.
Phishing comes in many shapes and forms, even phone calls. So stay vigilant and don’t react if you are in doubt. Hackers only need a split second’s access to your private key or recovery seed and it’s goodbye to your crypto.
Tip 3: Employ two-factor authentication (2FA)
It’s best to use two-factor authentication (2FA) for all of your accounts, from banking and crypto to social media and other services. You should also use an authenticator app to set up a phone-based 2FA rather than an email one, since your account could have been hacked without your knowledge.
However, you should avoid an SMS authenticator, as they are more easily compromised by means of a SIM swap, a scam that allows hackers to gain control of your telephone number. Something like Google Authenticator would be a better choice.
It’s also recommended that you restrict your API keys if you’re trading via third-party software. Setting them to only work with certain IP addresses will protect you in the event your secret keys are stolen.
Tip 4: Use a VPN
Without the use of a virtual private network (VPN), much of your online data is right out there for the taking. IP addresses, cookies, and other information can be easily vacuumed up by anyone with a keen interest in violating your privacy or making off with your crypto.
When you use a VPN, your IP address will be disguised, and you will generally be a much harder presence to track on the web. It’s highly recommended that anyone getting serious about crypto begin to browse the internet exclusively with a reputable VPN. There are of course also blockchain-native solutions like Web 3.0 platform Deeper Network at your disposal, which even allows you to earn some nice ERC20 and BEP20 DPR tokens in the process for sharing your bandwidth!
With the key players finally beginning to emerge, it’s a good time to take a look at some of the most important Web 3.0 projects set to really take off in 2022, each building out their own important corner of this new decentralized online paradigm: Helium, Deeper Network, Arweave, Polkadot, Ocean Protocol, and Theta Video API.
Tip 5: Set up several email addresses
Since there is always a chance your email will be either directly hacked or revealed in a larger data breach, it’s best not to keep all your sensitive info under one address. What makes much more sense is to have a layered system, where you keep the sensitive and non-sensitive data separated under different accounts.
A good rule of thumb is to keep your personal accounts, such as social media or shopping, distant from your financial accounts with banks or crypto entities. A further security step would be to then spread those financial accounts between several email addresses to eliminate a single point of failure.
Tip 6: Don’t brag about your crypto
We live in a dangerous world, and it’s far too easy for someone you told about your massive HODLings to physically force you to give up your private keys and make you transfer your money. Those who flex their crypto publically often become targets. Who can forget the infamous $2m Ian Balina hack of 2018 during a live stream?
Just last year, a man in Hong Kong was thrown out of a car and down a hillside after an in-person crypto meeting went sideways. In another incident, an entrepreneur in Spain was tortured for several hours in his own apartment by masked men and forced to hand over access to his accounts.
There’s no reason that anyone except your loved ones needs to know how well you’ve been doing in the markets. It’s usually best to take a modest approach in life, and in this case, it could make all the difference.
Tip 7: Get a hardware wallet
By far the safest way of all to store your crypto is to take it offline into cold storage with a hardware wallet (AKA cold wallet). That way, your private keys are inaccessible to hackers and thieves, and your storage solution is immune to computer viruses. You don’t want to keep all your crypto on exchanges, as even the mightiest of them have fallen victim to malicious exploitations over the years.
What you really should look for is a hardware wallet with a Secure Element (SE) microchip, such as those made by CoolWallet. As of 2021, there is now even in-app support for NFT trading platforms such as Rarible and OpenSea. The CoolWallet S with its biometric verifications, encrypted Bluetooth and EAL5+ SE gets the job done very well for most people, but the flagship CoolWallet Pro (with its industry gold standard EAL6+ SE) is an excellent choice for anyone looking to get into more DeFi opportunities as well. The need to physically validate transactions through a button push on the device and 10m maximum distance between wallet and phone ensures that if your app is penetrated, you still have an impenetrable last line of defense between the bad guys and your crypto. Use it!
Final Thoughts
While cold wallets offer superior protection against hacks and scams thanks to their offline storage and custom features like a secure element, the human element involved in wallet security always created opportunities for exploits. Wallet owners are still susceptible to info-stealing phishing schemes and other attacks that rely on deception or resort to physical violence like the scary $5 wrench attack. Still, far and away, they are the best defense against crypto criminals. Most importantly, make sure you use common sense and keep sensitive wallet information offline and somewhere secret and safe at all times.
Source: CoolWallet.io, HardwareWallets-Guide.com
7 TOP Tips for Crypto Wallet Security
Learn more about the best TOP 30 hardware cryptocurrency wallets
You can see this list here.
TOP 29 Hardware Wallets, the Official Online Stores
| 1 |  | Trezor hardware wallet, the official online store |  |
| 2 |  | Ledger hardware wallet, the official online store |  |
| 3 |  | KeepKey hardware wallet, the official online store |  |
| 4 |  | BitBox02 hardware wallet, the official online store |  |
| 5 |  | CoolWallet hardware wallet, the official online store |  |
| 6 |  | ELLIPAL hardware wallet, the official online store |  |
| 7 |  | D'CENT hardware wallet, the official online store. |  |
| 8 |  | SafePal hardware wallet, the official online store |  |
| 9 |  | SecuX hardware wallet, the official online store |  |
| 10 |  | BC Vault hardware wallet, the official online store |  |
| 11 |  | BitLox hardware wallet, the official online store |  |
| 12 |  | Keystone hardware wallet, the official online store |  |
| 13 |  | ProKey hardware wallet, the official online store |  |
| 14 |  | NGRAVE hardware wallet, the official online store |  |
| 15 |  | Keevo hardware wallet, the official online store |  |
| 16 |  | GridPlus hardware wallet, the official online store |  |
| 17 |  | Ballet hardware wallet, the official online store |  |
| 18 |  | OPOLO hardware wallet, the official online store |  |
| 19 |  | Foundation (Passport) hardware wallet, the official online store |  |
| 20 |  | ImKey hardware wallet, the official online store |  |
| 21 |  | Tangem hardware wallet, the official online store |  |
| 22 |  | HashWallet hardware wallet, the official online store |  |
| 23 |  | Material Bitcoin hardware wallet, the official online store |  |
| 24 |  | ShieldFolio hardware wallet, the official online store |  |
| 25 |  | OneKey hardware wallet, the official online store |  |
| 26 |  | Blockstream Jade hardware wallet, the official online store |  |
| 27 |  | Cypherock hardware wallet, the official online store |  |
| 28 |  | Keepser hardware wallet, the official online store |  |
| 29 |  | NEXA hardware wallet, the official online store |  |
TOP 20 Best Metal Cold Storage Seed Phrase Backups, the Official Online Stores
The opinions of the author and information available in this article are shared for educational and entertainment purposes only and should not be considered as financial or security advice of any kind. Always do your own research in order to best protect yourself and your financial assets.